Cybersecurity
Provide a safe working environment for your employees
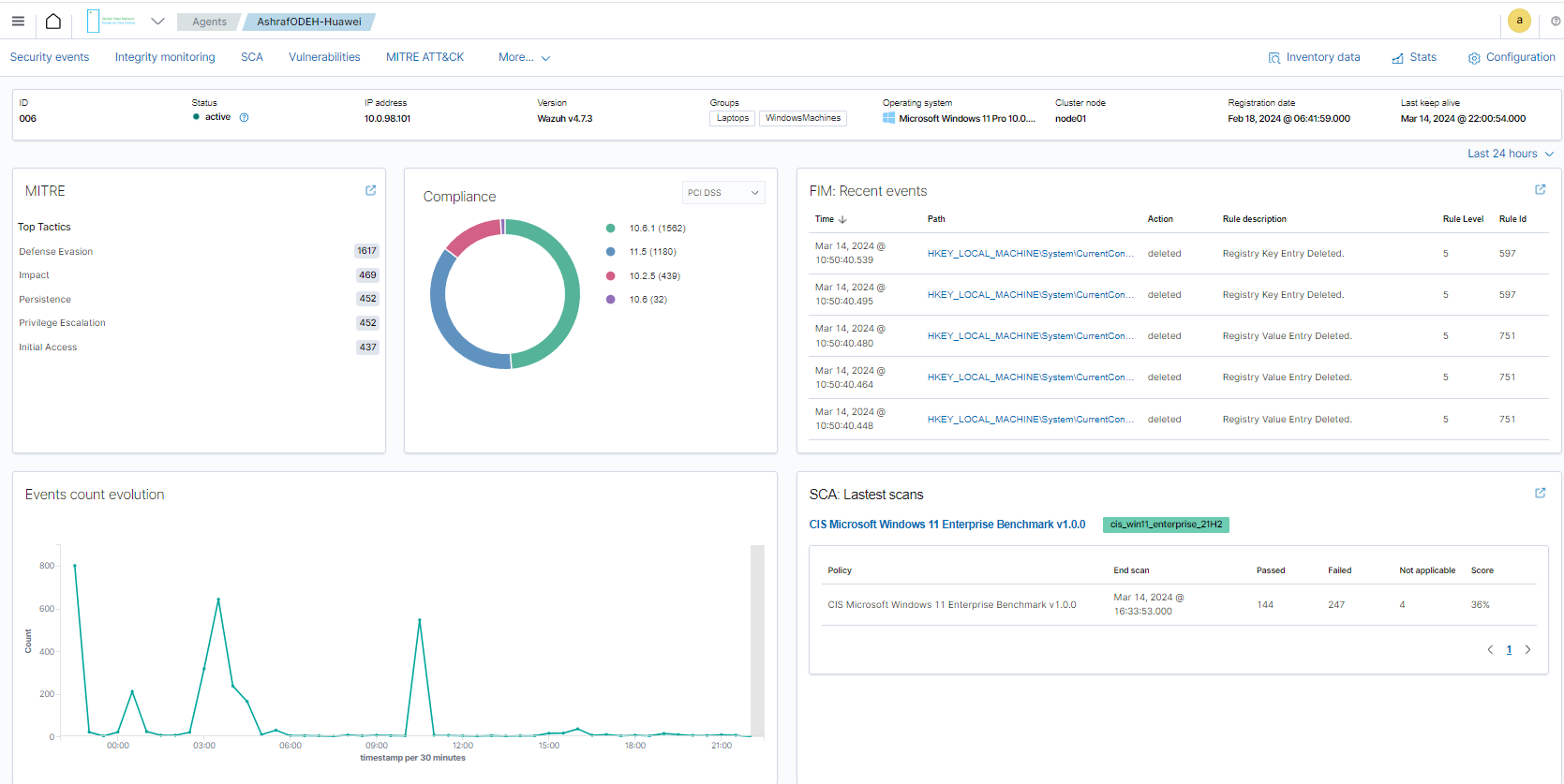
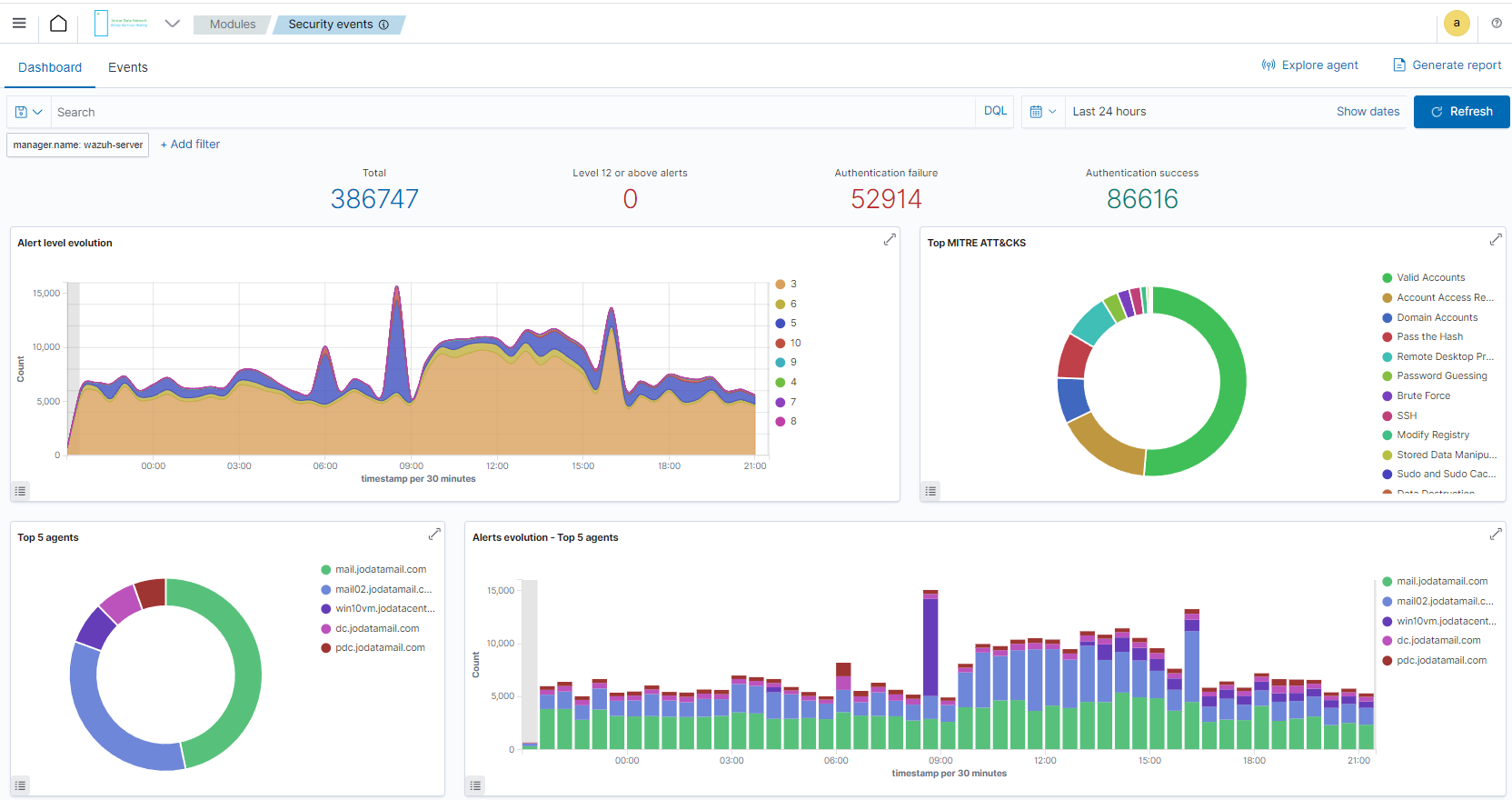
Security Events
Identify issues and threats to your environment — devices (laptops, PCs, and servers) and perform necessary remediation tasks.
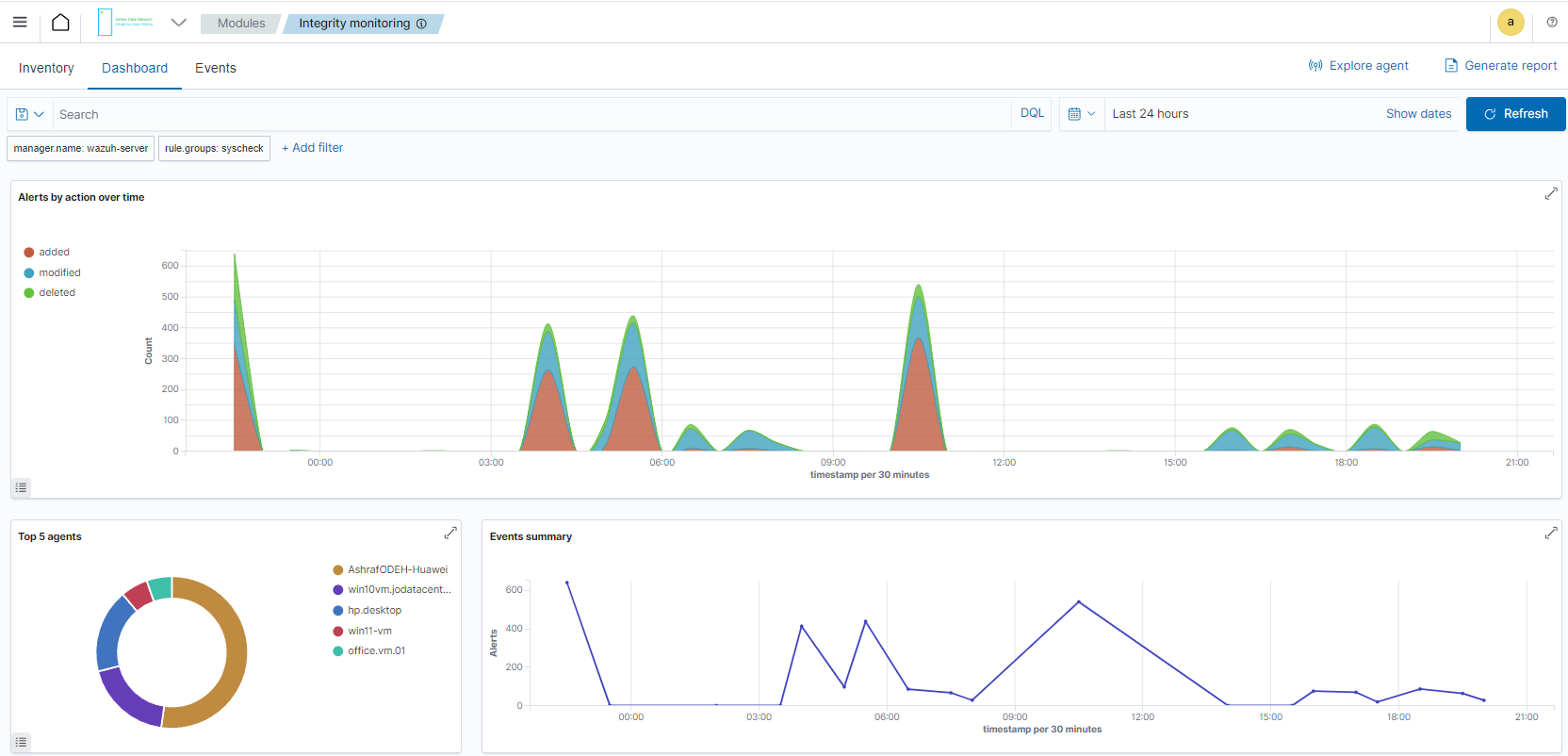
Integrity Monitoring
Alerts related to file changes, including permissions, content, ownership and attributes.
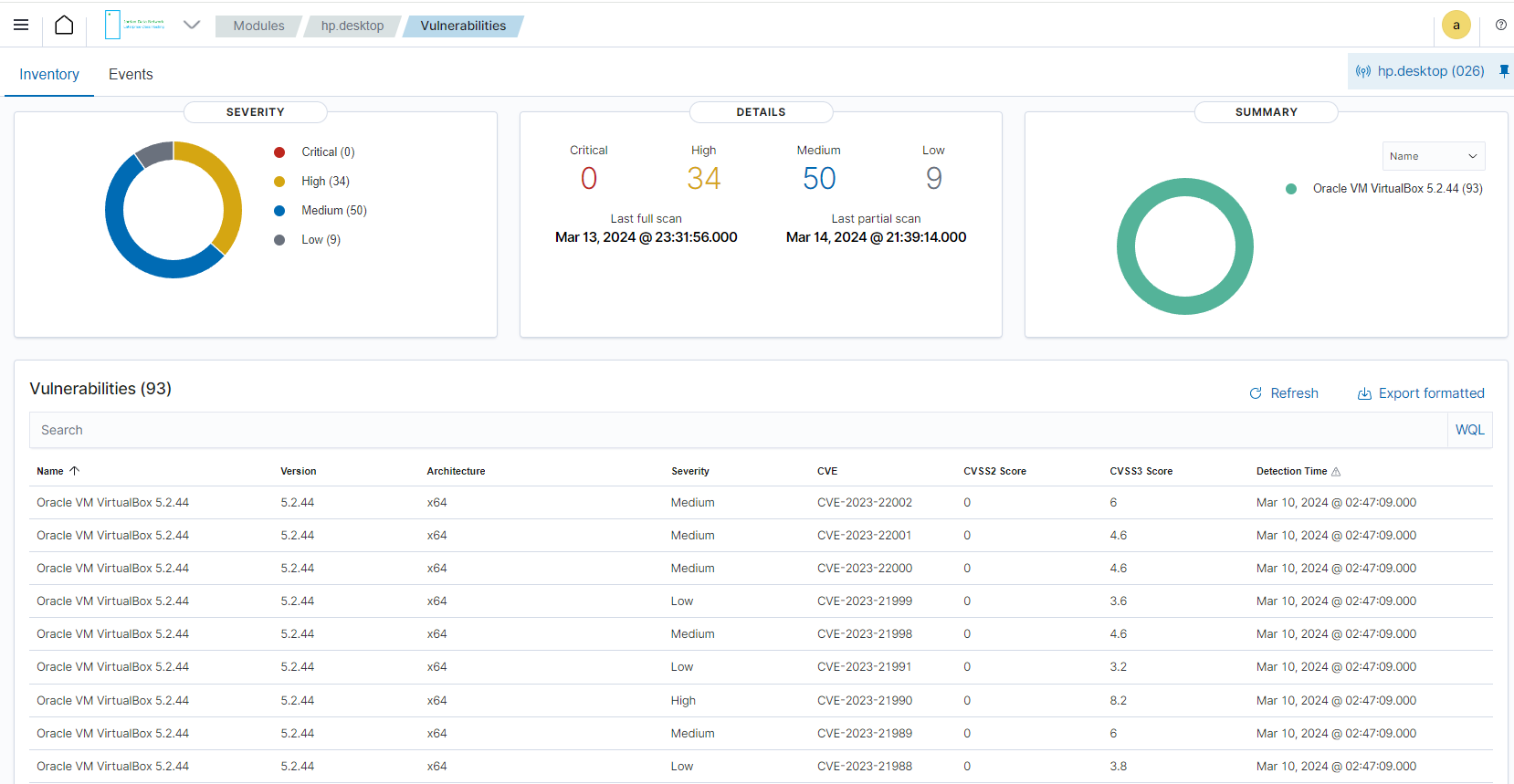
Vulnerabilities
Discover what applications in your environment are affected by well-known vulnerabilities.
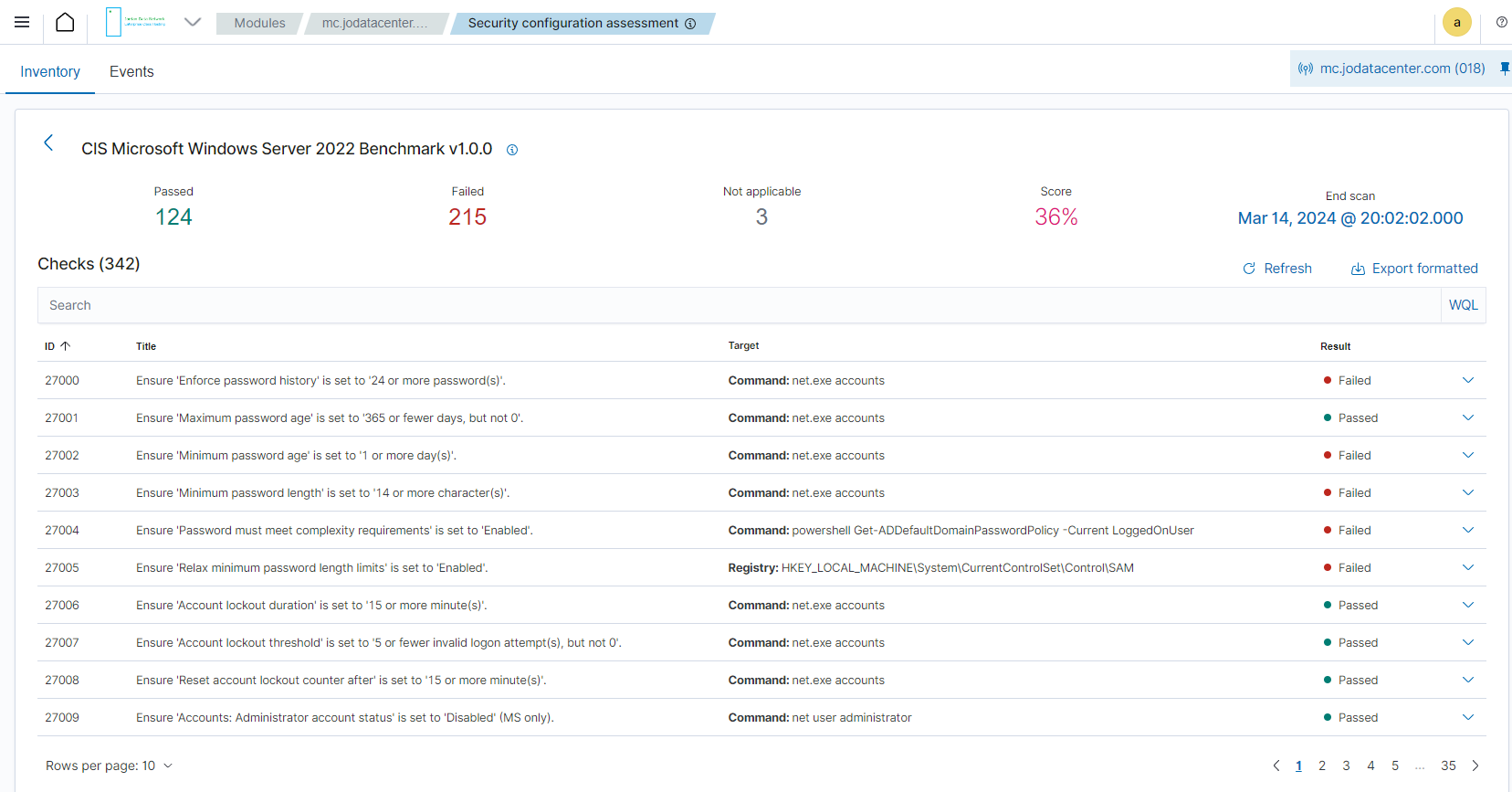
Security Configuration Assessment
Scan your assets as part of a configuration assessment audit.
System Auditing
Audit users behavior, monitoring command execution and alerting on access to critical files.